What is my Current Lab Project?
So, for my first blog post I thought I would start off with a question many people in the security field get. What are you working on in your lab?
That answer is a project in the Identity and Access Management domain. The intent of this project is three pronged. I first want to determine the usability Microsoft Windows Server Core 2019 in an Active Directory Infrastructure. Then I want to give my helpdesk personnel all the tools necessary to do their job, while restricting their access to deeper levels of the infrastructure, as in removing Domain Admin privileges. The last goal is the implementation of LAPS on all endpoints.
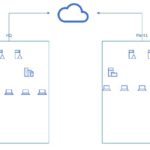
This virtual company has a Headquarters and Plant 1. Each location has two Domain Controllers, two servers with GUI, as well as five PCs. Each location has an OU for HR, IT, Accounting, and Production. Please see my rough Visio drawing of my virtual environment.
The first prong of my intent is to learn all the ins and outs of Server Core. I want to build on my existing Windows Server skills buy understanding Sever Core at a deeper level. If I am the one spearheading Sever Core at company, I should be the subject matter expert. This will require me to learn more about the new Windows Admin Center, all the RSAT tools, and more PowerShell.
In my opinion, running Server Core on domain controllers provides additional security benefits. You maintain less of an attack surface, less patches, and you also have less of a chance of someone accidentally clicking and causing an availability issue as in oops, I shut down the domain controller instead of disconnecting.
The second prong of my intent is to limit the number of users who hold Domain Admin credentials. After some research, I found that Active Directory has some decent built in groups to allow for this. The primary group I zeroed in on is the Account Operators group. This group allows the person to create, delete, disable, and modify accounts. Most importantly, they can reset passwords. The downside is it also allows the assigned users to RDP to a domain controller. This can be denied with a simple GPO implementation. The other way to prevent the assigned users from doing this is to run Server Core.
The third prong of my intent is to implement LAPS in an Active Directory infrastructure that only runs Server Core. LAPS is Local Administrator Password Solution that is an included feature from Microsoft. As you may know, many organizations have the same static password for the local administrator account for every endpoint in their organization. This leads to a vulnerability called passed the hash. LAPS is a password manager that utilized Active Directory to manage and rotate password for all endpoints on your domain. I have currently implemented LAPS in two of my virtual labs and have tested it extensively. I am currently managing a project to implement it into production soon.
So, in closing, this is kind of a run down of my current lab project. Hopefully, I will be able to update my followers soon as I progress in the lab and provide more feedback on Server Core, Account Delegation, and LAPS.